Lessons I Learned From Info About How To Prevent Ip Spoofing

First, assess whether your phone number has indeed been spoofed.
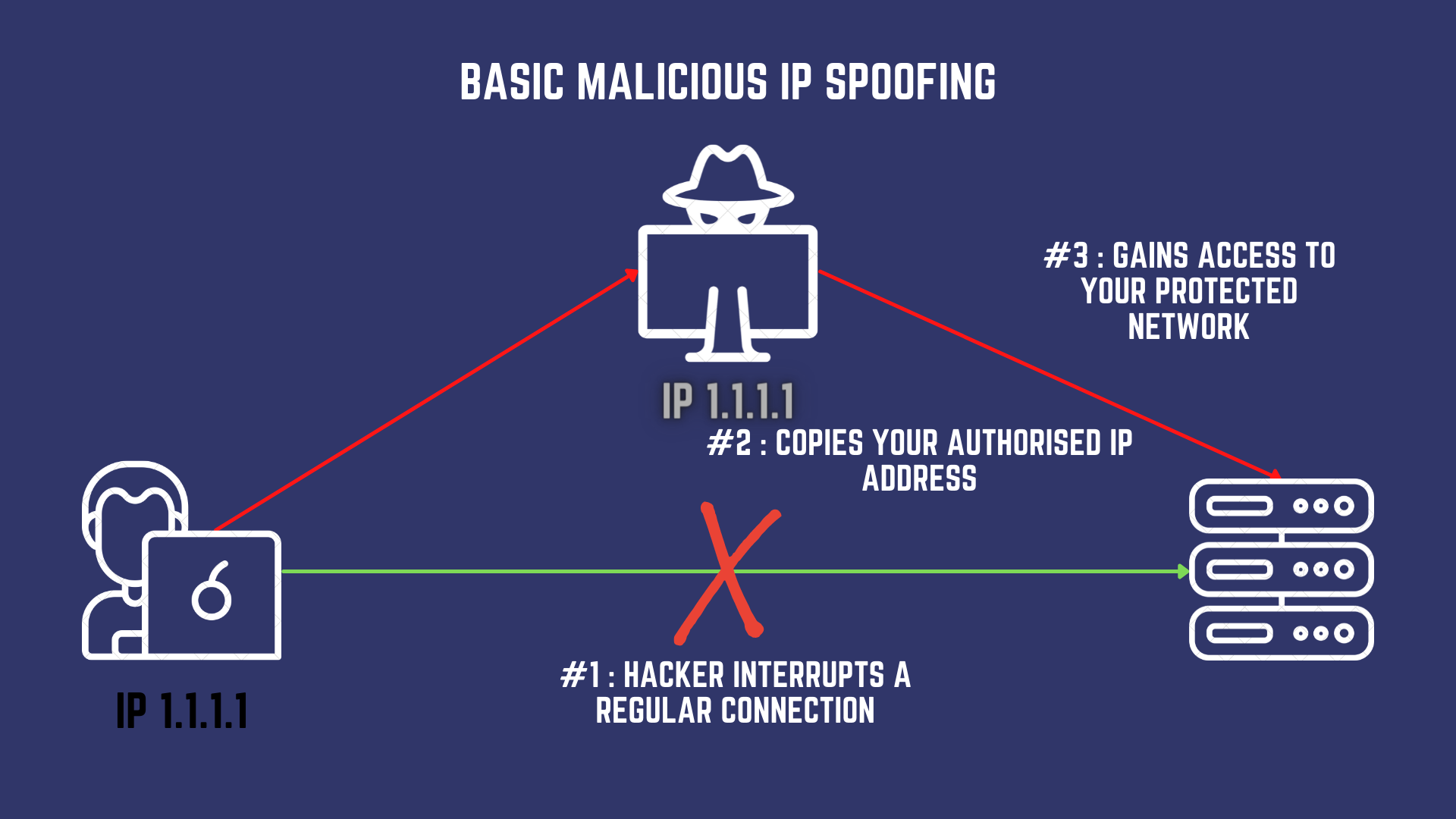
How to prevent ip spoofing. In the world of network security, spoofing has nothing to do with comedy movies. Spoofing is an impersonation of a user, device, or client on the internet. #1 bypass firewalls and ip authorization.
Recognizing email spoofing at an early stage prevents you from being victimized. It is often used during a cyberattack to disguise the source of. Instead, it’s a common and dangerous.
Before understanding ip address spoofing,. Then, monitor your network for suspicious activity with a firewall, which uses a packet filter that inspects ip packet headers. How to prevent spoofing attacks.
Ip spoofed packets can't be eliminated. After inserting the spf version tag v=spf1, you can add ip addresses of the mail server. To help prevent ip spoofing, you should use a vpn to hide your ip address.
Or you may have your. Whether you’re a private individual using the internet or you’re responsible for a local network: Connects hackers to an ip address through a spoofed address resolution protocol (arp) message, usually to enable denial of service (dos).
This approach prevents insiders from launching an ip spoofing attack. Find out how these scammers hijacked your phone number in the first place. It can come in various forms, so you.
Next, investigate how scammers gained access to your phone number. Ip spoofing allows cybercriminals to infect your computer with malware, steal your. In the vast expanse of the digital realm, where every click.
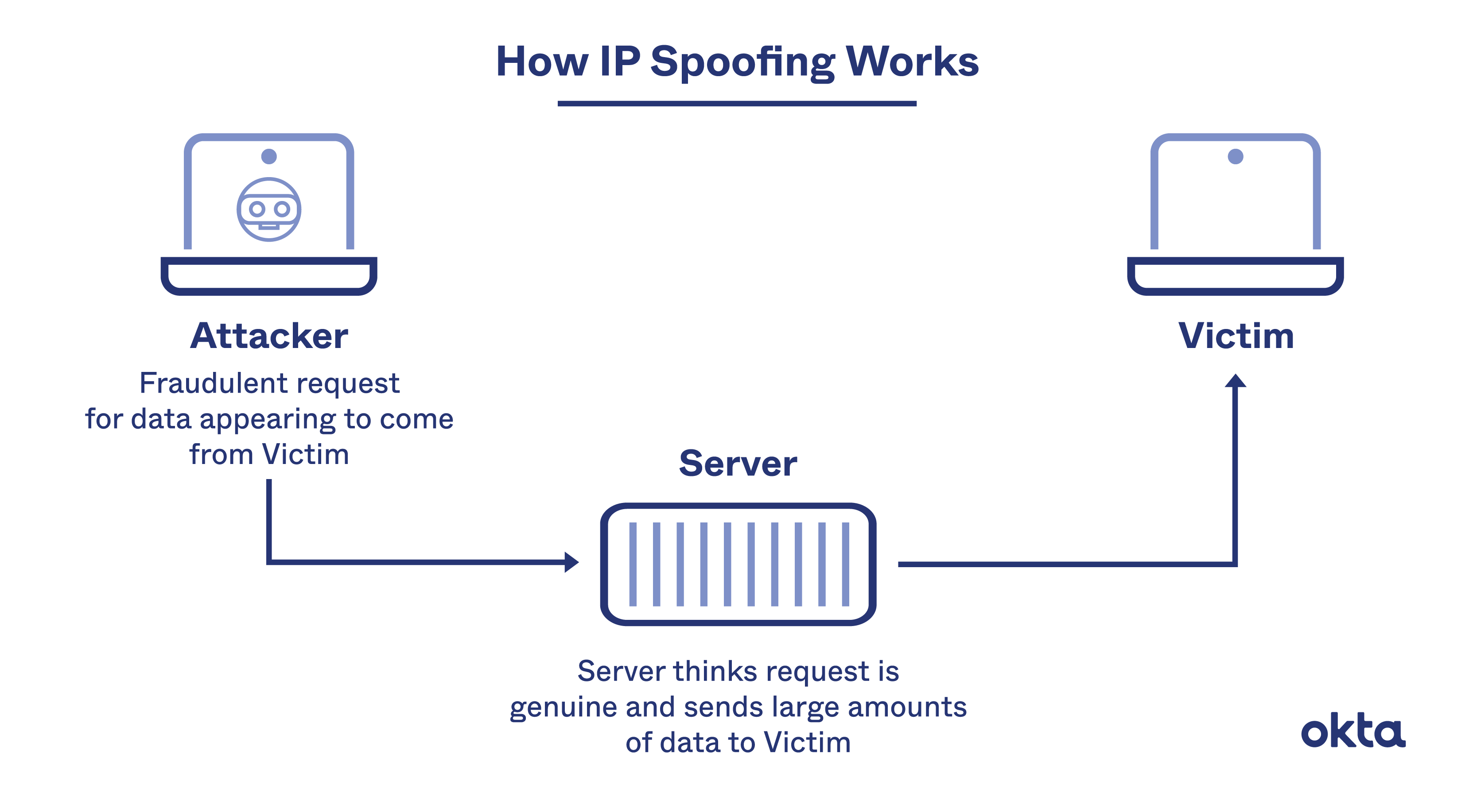
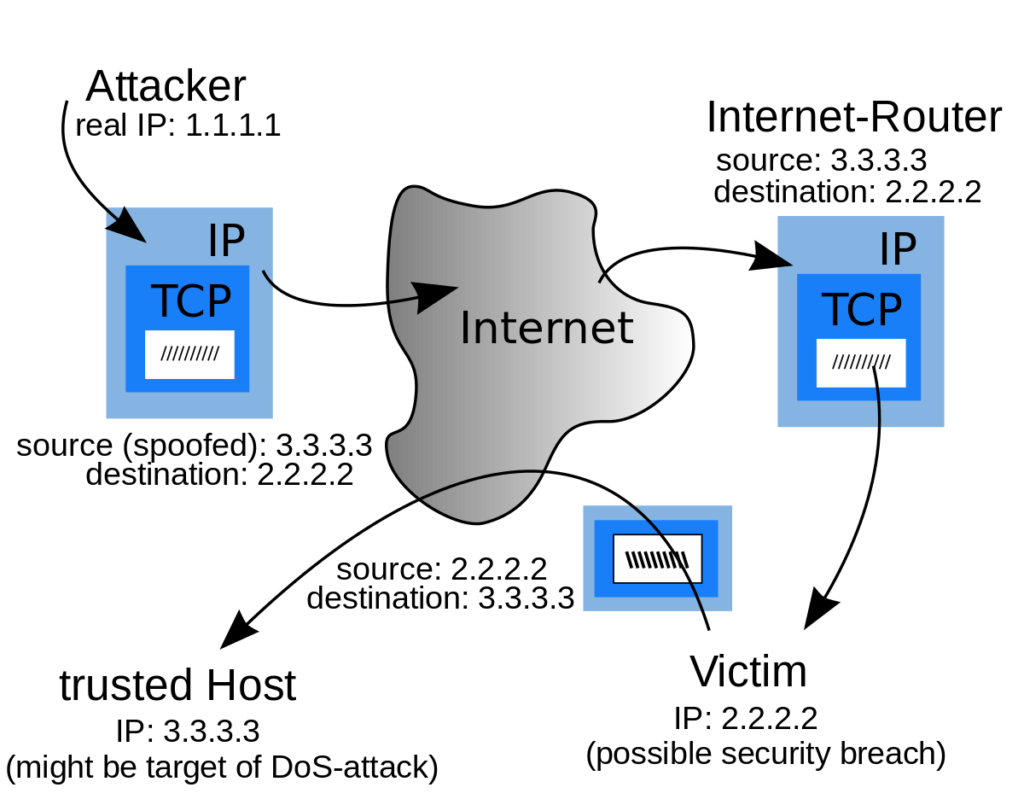
As computer safety protocols increase, cybercriminals must get increasingly. As we use different mail servers, please login the sosafe manager portal. Ip spoofing, also known as ip address spoofing, is a technique used in computer networking to manipulate the source ip address in a packet’s header.
Your number may have been leaked in a data breach. How do you protect against ip spoofing? Ip address spoofing:
November 25, 2020 3 min read. There are five things, among others, that you can do to help prevent ip spoofing and its related attacks from affecting your network: Continue reading to learn more about spoofing attacks, the seven common types of spoofing attacks and how to stay protected from them.